
Hackers aren’t just characters in thrillers—they’re out there, looking for easy targets every day. With cyber threats evolving faster than ever, staying safe online is no longer optional. But don’t worry; protecting yourself doesn’t require a degree in cybersecurity. These 20 smart habits can keep you digitally safe.
Use Strong And Unique Passwords For Every Account

Cracking weak passwords takes seconds, making security a serious concern. In 2023, 123456 remained the most hacked password, with over 23 million breaches. Hackers rely on brute-force tools to test common passwords within minutes. To stay secure, use long and unique combinations.
Turn On Two Factor Authentication For Extra Security
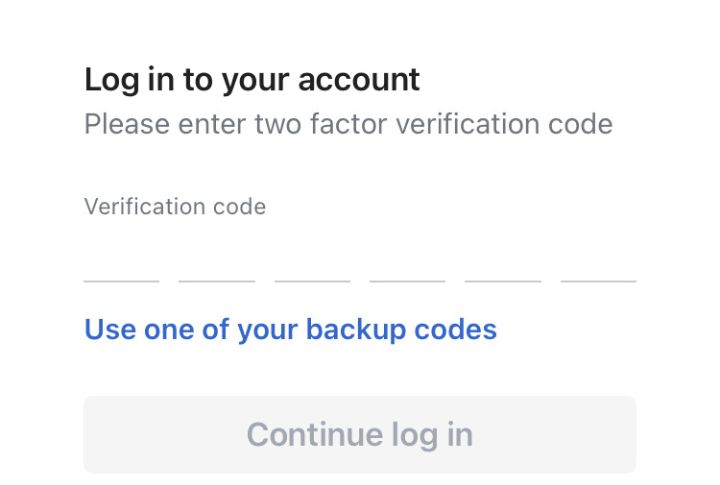
A password alone won’t cut it. Enabling two-factor authentication (2FA) blocks 99.9% of automated attacks. It requires an extra code, usually sent via text, email, or an authentication app. Even if hackers get access to your password, they can’t access your account. Without 2FA, they’re one lucky guess away.
Think Twice Before Clicking On Suspicious Links

Do you know that over 3.4 billion phishing emails are sent daily? Hackers rely on fear and haste to breach data, making quick decisions risky. Always check for misspelled URLs, and if an email demands immediate action, pause. A single careless click can compromise everything—stay alert to stay safe.
Keep Software And Apps Updated

Outdated software is a hacker’s playground. In 2017, the WannaCry ransomware attack exploited an unpatched Windows flaw, infecting 230,000 computers worldwide. Updates close security gaps and defend against evolving threats, making automatic updates a critical safeguard. Skipping them leaves doors wide open for attackers.
Avoid Using Public Wi-Fi For Sensitive Transactions

Public Wi-Fi networks lack encryption, making data easy to intercept. Hackers exploit this weakness with man-in-the-middle attacks to spy on users, intercept logins, and even inject malware. Avoid accessing banking apps or entering passwords on public Wi-Fi.
Enable A Password Manager To Store Credentials Securely
Writing passwords on sticky notes? A hacker’s dream. Weak storage habits make it easy for cybercriminals to access sensitive accounts. A password manager encrypts credentials, generating strong, unique logins for every account and reducing the risk of widespread leaks. It also protects against keyloggers by auto-filling credentials only on verified sites.
Set Up Automatic Backups To Protect Your Data

The average cost of a cyberattack for businesses is $4.35 million per breach, making data protection essential. Regular backups ensure recovery after cyber incidents and prevent permanent loss. To safeguard critical files, use external hard drives or cloud storage with end-to-end encryption. Without a backup, stolen data may be gone forever.
Use A Virtual Private Network For Added Privacy

Internet traffic without encryption is like sending postcards—anyone can read them. A Virtual Private Network (VPN) protects online activity by routing traffic through secure servers, blocking ISPs, hackers, and advertisers from tracking data. However, free VPNs often sell user information, so choosing a reputable provider with a strict no-logs policy is best.
Watch For Unexpected Account Activity And Alerts

Cybercriminals often remain hidden, but signs like unfamiliar logins or unrecognized purchases can signal a breach. Hackers use stolen credentials for credential-stuffing attacks, attempting logins across multiple sites. Tools like “Have I Been Pwned” let users check if their email has been compromised in a breach.
Be Mindful Of Browser Extensions
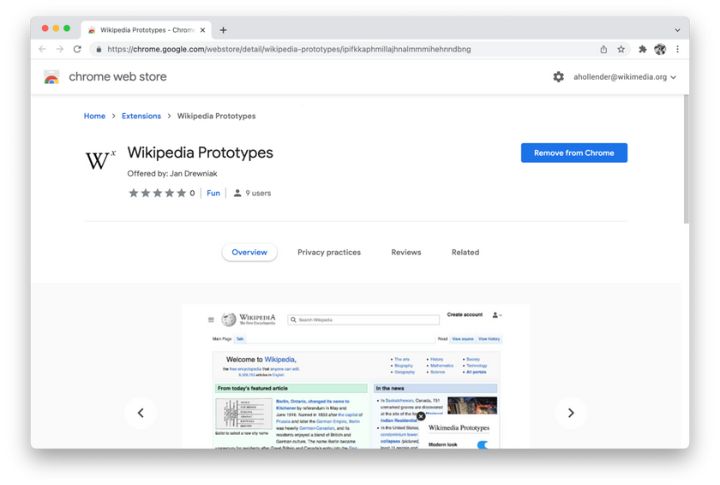
Browser extensions offer great functionality, but they can also present security vulnerabilities if not carefully controlled. Harmful extensions have the potential to monitor your online behavior or insert malicious code into your browsing. Regularly review and remove unnecessary or suspicious extensions to maintain security and protect your privacy.
Be Cautious When Sharing Personal Information Online
Cybercriminals mine social media for personal details like birthdays, locations, and pet names—common password reset answers. A seemingly harmless post about a childhood nickname or favorite vacation spot can give hackers the clues they need to bypass security measures. Limit what you share online and avoid posting sensitive details to stay safe.
Turn Off Bluetooth When Not In Use

Bluetooth exploits allow hackers to intercept connections within 30 feet. Attackers use Bluebugging to hijack devices and make unauthorized calls. In public, disable Bluetooth when it’s unnecessary. A hacker needs only a few seconds to connect to an open device—keeping it off keeps them out.
Delete Unused Apps

Old apps harbor unpatched vulnerabilities, making them easy targets for hackers. Without regular security updates, outdated software exposes devices to malware and unauthorized access. If an app hasn’t received updates in months, it’s best to delete it, as abandoned apps often contain unresolved security flaws.
Avoid Using The Same Email For Everything
Using separate emails for financial accounts, shopping, and general communication adds an extra layer of security. Relying on a single email for everything makes hacking easier—if it’s breached, hackers can access multiple logins with minimal effort. Financial accounts, in particular, should be tied to a private email that isn’t used for everyday sign-ups or social media.
Check For HTTPS Before Entering Sensitive Information

Cybercriminals often create fake login pages that look legitimate but lack HTTPS, tricking users into entering passwords and payment details. Always look for the padlock logo in the address bar before entering sensitive information, and avoid unsecured sites altogether. If a site lacks HTTPS, it’s best to assume it’s unsafe.
Lock Your Devices To Prevent Unauthorized Access

In the U.S., one laptop is stolen every 53 seconds, and many thefts target public places like coffee shops and airports. A strong passcode or biometric lock, such as a fingerprint, is the first line of defense. However, security doesn’t stop there—enable remote wipe features on other devices to erase data if the device falls into the wrong hands
Do Not Open Attachments From Unknown Senders

Email attachments remain the top method for delivering malware, often disguising malicious code within seemingly harmless files such as PDFs. Attackers craft emails to appear urgent, impersonating banks or government agencies to trick recipients into opening infected files. If an email appears suspicious, use a trusted source to verify the sender instead of replying.
Clear Your Browser Cache And Cookies Regularly

Hackers can track your online activity through cookies and stored data in your browser cache. Make it a habit to clear your browser’s cache and cookies regularly, especially after logging into sensitive accounts. This minimizes the risk of being tracked or exposed to attacks like session hijacking.
Secure Smart Home Devices To Prevent Cyber Intrusions

Smart TVs or cameras are prime hacking targets, often overlooked in home security. Several smart devices come with default passwords that are easily guessed or publicly available, giving hackers a way in. To reduce risks, change default passwords immediately and turn off unnecessary features like remote access if not needed.
Sign Out Of Accounts When Finished Using Them

Staying logged in on shared or public devices risks exposure. Many attacks exploit open sessions, letting hackers gain access without needing passwords. Public computers and even friends’ devices aren’t secure. Logging out helps prevent unauthorized access, making it harder for intruders to hijack accounts.
